How Network Penetration Testing Works
In today’s digital age, information security services are paramount for businesses to protect their sensitive data and systems from cyber threats. One of the crucial aspects of information security is Network Penetration Testing. This practice involves simulating cyber attacks to identify vulnerabilities in a network’s defences. Let’s delve deeper into how Network Penetration Testing works and explore its different types.
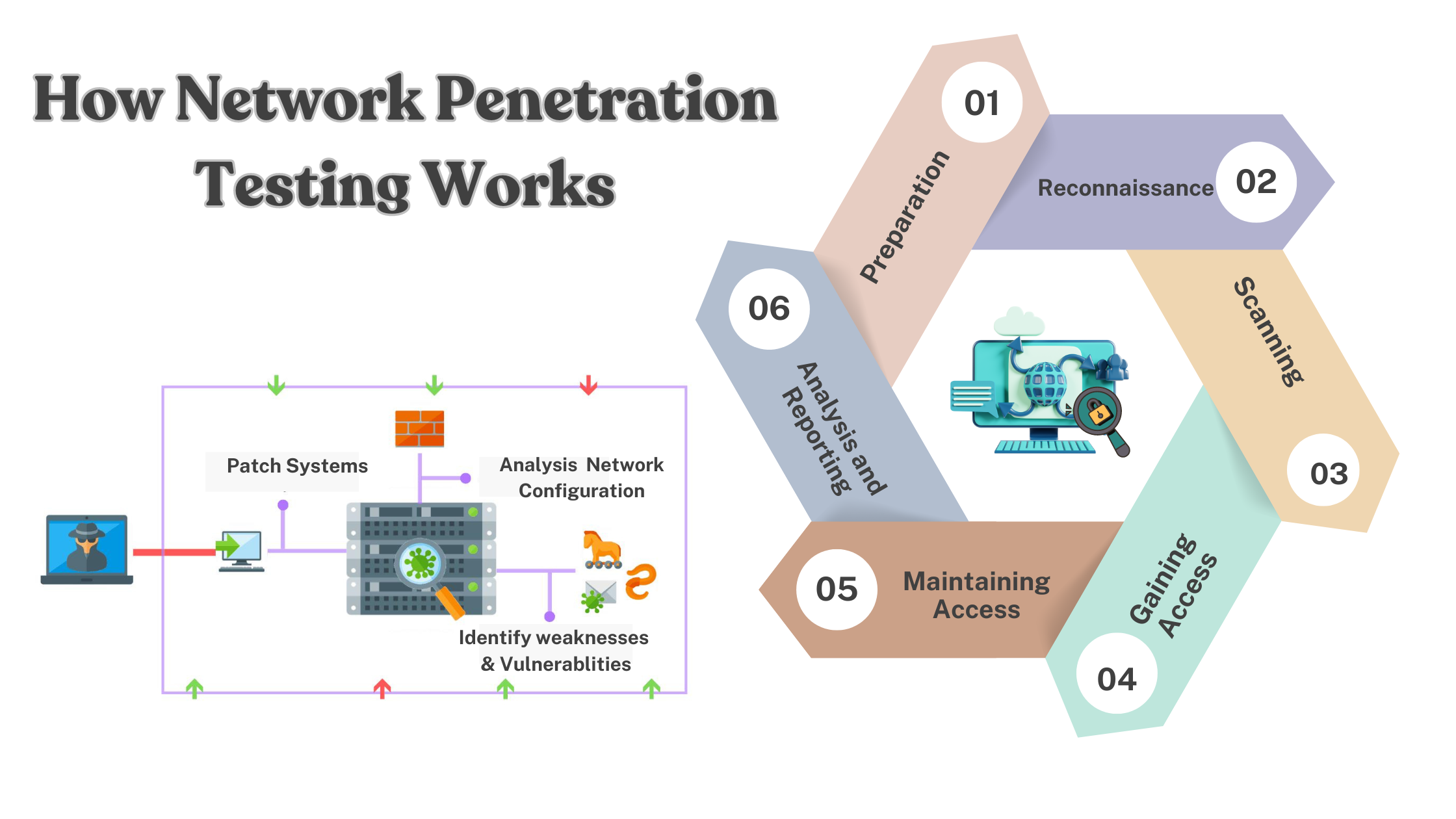
Preparation: The process begins with defining the scope and objectives of the test. This includes identifying the systems, applications, and network components to be tested, as well as determining the testing methods to be used.
Reconnaissance: This phase involves gathering information about the target network. It includes passive reconnaissance, where publicly available data like domain names and IP addresses are collected, and active reconnaissance, where tools like port scanners and network mappers are used to discover live hosts and open ports.
Scanning: In this stage, vulnerability scanners are employed to identify potential weaknesses in the network, such as outdated software versions, misconfigurations, or known vulnerabilities.
Gaining Access: Penetration testers attempt to exploit the identified vulnerabilities to gain unauthorized access to the network. This may involve techniques like password cracking, SQL injection, or exploiting unpatched software.
Maintaining Access: Once access is gained, testers aim to maintain their presence within the network without being detected. This helps assess the network’s ability to detect and respond to intrusions.
Analysis and Reporting: After the testing is complete, a detailed report is generated outlining the vulnerabilities discovered, the methods used to exploit them, and recommendations for mitigating these risks.
Different Types of Network Penetration Testing
Black Box Testing: Also known as blind testing, this approach simulates an attack by an external hacker who has no prior knowledge of the target network. It helps assess how well the network’s defenses can withstand an external threat.
White Box Testing: In contrast to black box testing, white box testing provides testers with full knowledge of the network’s architecture, source code, and configurations. This enables a more thorough assessment of the network’s security posture.
Gray Box Testing: This method combines aspects of both black box and white box testing. Testers have partial knowledge of the network, allowing them to simulate attacks from both internal and external threats.
Internal Testing: Internal penetration testing focuses on assessing the security of internal network resources, such as servers, workstations, and databases. It helps identify vulnerabilities that could be exploited by insiders or attackers who have gained internal access.
External Testing: External penetration testing evaluates the security of external-facing systems, such as web servers, email servers, and VPN gateways. It aims to identify vulnerabilities that could be exploited by external attackers to gain unauthorized access.
Targeted Testing: Also known as focused testing, this type of penetration testing concentrates on specific areas or assets within the network, such as critical servers or sensitive data repositories. It allows organizations to prioritize security efforts based on the importance of their assets.
Social Engineering Testing: Social engineering testing involves using psychological manipulation techniques to trick employees into revealing sensitive information or performing actions that compromise security. This type of testing helps assess the effectiveness of security awareness training and policies.
Advanced Techniques in Network Penetration Testing
Network Penetration Testing is a dynamic field that continuously evolves to keep pace with emerging cyber threats and technologies. In addition to the fundamental aspects discussed earlier, there are several advanced techniques and considerations that penetration testers employ to enhance the effectiveness of their assessments. Let’s explore some of these advanced techniques and their significance in the context of Network Penetration Testing.
Exploitation Frameworks: Penetration testers often utilize exploitation frameworks such as Metasploit, Cobalt Strike, and Canvas to automate and streamline the process of exploiting vulnerabilities. These frameworks offer a wide range of tools and payloads to execute targeted attacks and gain access to vulnerable systems.
Post-Exploitation: Beyond gaining initial access, testers focus on post-exploitation activities to escalate privileges, maintain persistence, and exfiltrate sensitive data. Techniques like privilege escalation, lateral movement, and data exfiltration simulations are essential to simulate real-world attack scenarios.
Fileless Attacks: Fileless attacks, also known as memory-based attacks, leverage in-memory techniques to avoid detection by traditional antivirus solutions. Penetration testers simulate fileless attacks to assess the network’s ability to detect and respond to advanced threats that bypass conventional security measures.
Web Application Testing: In addition to network-level testing, penetration testers assess the security of web applications by conducting thorough tests for vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR). Web application testing complements network testing to provide a comprehensive security assessment.
Cloud-Based Testing: With the widespread adoption of cloud services, penetration testers now focus on evaluating the security of cloud environments, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) offerings. Cloud-based testing involves assessing configuration errors, access controls, and data encryption practices within cloud platforms.
Red Team Exercises: Red team exercises go beyond traditional penetration testing by simulating full-scale cyber attacks orchestrated by skilled adversaries. Red teams emulate the tactics, techniques, and procedures (TTPs) of threat actors to test an organization’s detection and response capabilities comprehensively.
IoT and OT Testing: With the proliferation of Internet of Things (IoT) devices and operational technology (OT) systems, penetration testers focus on assessing the security of these interconnected devices and industrial control systems (ICS). IoT and OT testing involve identifying vulnerabilities in firmware, communication protocols, and access controls.
Compliance Testing: Penetration testers align their assessments with regulatory requirements and industry standards such as PCI DSS, HIPAA, GDPR, and NIST cybersecurity frameworks. Compliance testing ensures that organizations meet legal and regulatory obligations while enhancing their overall security posture.
Significance of Advanced Techniques
Real-World Simulation: Advanced techniques enable penetration testers to simulate sophisticated cyber attacks that closely mimic real-world threats. This realism enhances the accuracy and relevance of security assessments.
Comprehensive Risk Assessment: By incorporating advanced techniques, testers can uncover hidden vulnerabilities, exploit complex attack vectors, and assess the impact of successful breaches on critical assets. This comprehensive risk assessment helps organizations prioritize security investments and remediation efforts.
Continuous Improvement: Embracing advanced techniques in Network Penetration Testing promotes a culture of continuous improvement in cybersecurity practices. Testers leverage cutting-edge tools, methodologies, and threat intelligence to stay ahead of evolving threats and vulnerabilities.
Enhanced Defense Strategies: Insights gained from advanced penetration testing techniques empower organizations to develop and implement proactive defense strategies. This includes fine-tuning intrusion detection systems (IDS), implementing robust access controls, and enhancing incident response capabilities.
Conclusion
Network Penetration Testing stands as a critical pillar in modern information security services, offering organizations a proactive approach to identifying and mitigating cyber threats. Through a structured process encompassing preparation, reconnaissance, scanning, gaining access, maintaining access, analysis, and reporting, businesses can gain invaluable insights into their network’s vulnerabilities and security posture.
The diverse types of Network Penetration Testing, including Black Box, White Box, Gray Box, Internal, External, Targeted, and Social Engineering Testing, cater to various security needs, ensuring a comprehensive evaluation of both internal and external threats.
Moreover, the adoption of advanced techniques such as exploitation frameworks, post-exploitation strategies, fileless attacks simulation, web application testing, cloud-based assessments, red team exercises, IoT and OT testing, and compliance testing elevates the effectiveness and relevance of penetration testing in today’s dynamic threat landscape.
Ultimately, Network Penetration Testing, coupled with advanced techniques, fosters a culture of continuous improvement, empowers organizations to make informed security decisions, and strengthens their defense strategies against evolving cyber threats. Embracing these practices is not just a proactive measure but a strategic imperative in safeguarding sensitive data and maintaining trust in the digital age.