How to Perform Mobile Application Penetration Testing
In today’s digital landscape, mobile applications have become an integral part of our daily lives, facilitating everything from banking to social networking. As their usage increases, so does the need for robust security measures to protect sensitive user data. This is where information security services, particularly mobile application penetration testing, come into play. In this blog, we will explore the essential steps to perform mobile application penetration testing and the best tools available for this purpose..
What is Mobile Application Penetration Testing?
Mobile application penetration testing (pen-testing) is a systematic process of evaluating the security of a mobile app by simulating attacks that a malicious user might carry out. The aim is to detect and resolve vulnerabilities before they can be exploited. Pen-testing helps ensure that the application is secure against potential threats and complies with industry standards and regulations.
Why is Mobile Application Penetration Testing Important?
- Data Protection: Mobile apps often handle sensitive user information such as personal details, financial data, and health records. Pen-testing helps safeguard this information from unauthorized access and breaches.
- Regulatory Compliance: Many industries require compliance with specific security standards. Pen-testing ensures that the app meets these regulatory requirements.
- Reputation Management: Security breaches can significantly damage a company’s reputation. Regular pen-testing helps maintain user trust by ensuring the app is secure.
- Preventing Financial Losses: Security breaches can lead to substantial financial losses due to legal penalties, compensations, and loss of business. Pen-testing helps prevent these losses by identifying and mitigating vulnerabilities.
Steps to Perform Mobile Application Penetration Testing
Performing mobile application penetration testing involves several key steps, which can be broadly categorized into preparation, execution, and reporting.
1. Preparation
a. Define the Scope
Determine the scope of the pen-test by identifying which parts of the application will be tested. This includes specifying the platforms (iOS, Android), application versions, and any backend services that need to be included.
b. Gather Information
Collect all necessary information about the application, such as architecture, data flow, functionality, and user roles. This helps in understanding how the application operates and where potential vulnerabilities might exist.
c. Set Up the Testing Environment
Make sure the testing environment closely replicates the production environment. This includes setting up devices, emulators, and any required network configurations.
2. Execution
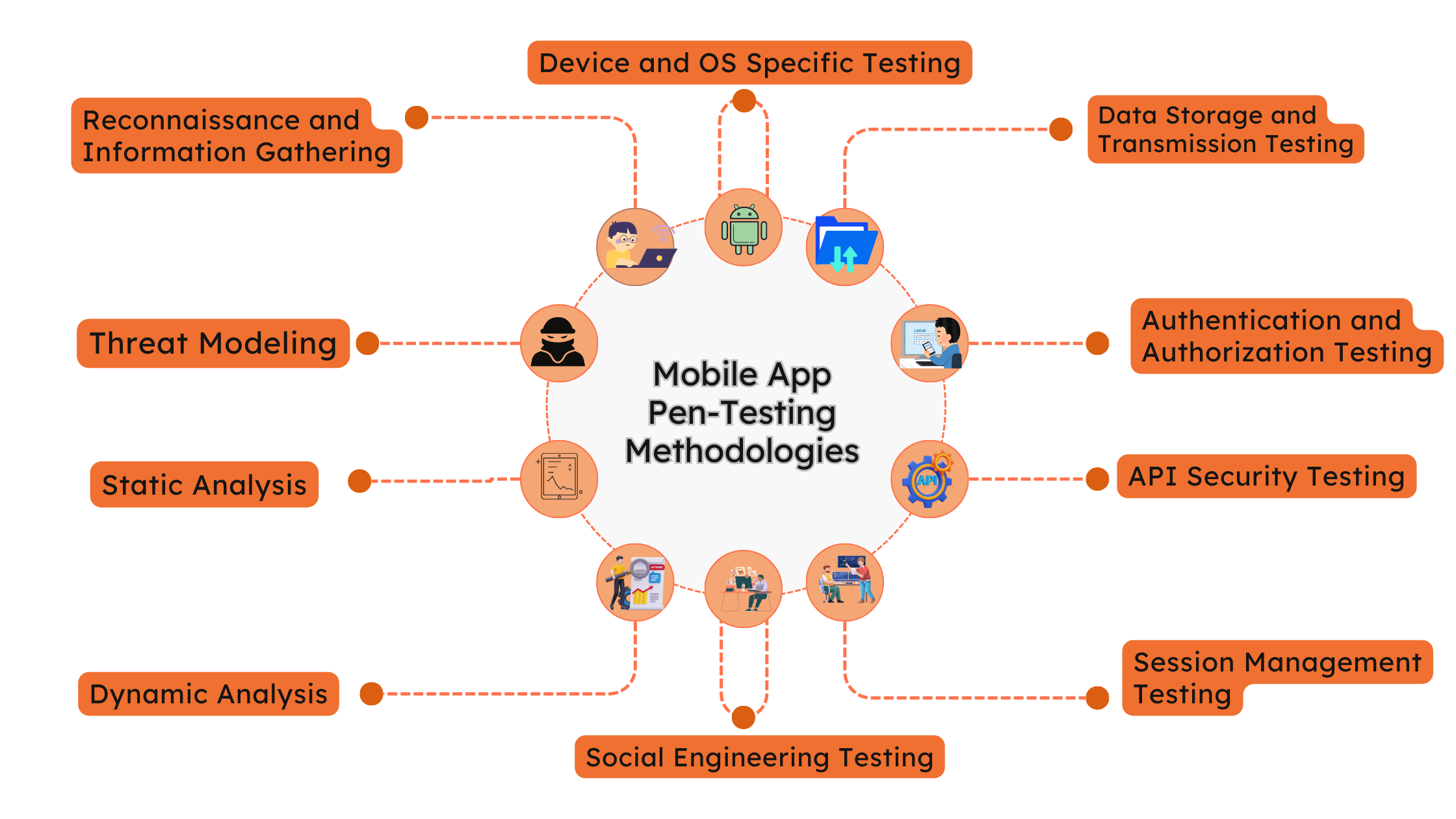
a. Static Analysis
Source Code Review: If the source code is available, review it for security vulnerabilities. Look for issues such as hardcoded credentials, insecure data storage, and improper error handling.
Binary Analysis: Analyze the compiled binary files for security issues. Tools like MobSF (Mobile Security Framework) can be used for this purpose.
b. Dynamic Analysis
Runtime Analysis: Monitor the app during execution to identify vulnerabilities that may not be apparent in static analysis. This includes testing for issues like insecure data transmission, improper session handling, and unauthorized access.
Reverse Engineering: Decompile the application to understand its logic and identify potential vulnerabilities. Tools like JADX and Ghidra can be used for reverse engineering.
c. Network Communication Analysis
Intercept Traffic: Use tools like Burp Suite or OWASP ZAP to intercept and analyze the traffic between the app and backend servers. Look for insecure data transmission, weak encryption, and sensitive data leaks.
d. API Testing
Assess APIs: Test the APIs used by the mobile app for security vulnerabilities. Check for issues like improper authentication, insufficient authorization, and data leakage.
Automate API Testing: Use tools like Postman and SoapUI to automate API testing.
e. Exploitation
Simulate Attacks: Simulate real-world attacks to exploit identified vulnerabilities. This includes testing for SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR).
Privilege Escalation: Test for vulnerabilities that could allow attackers to escalate their privileges within the application.
3. Reporting
a. Document Findings
Detailed Report: Document all identified vulnerabilities, including a description of the issue, its impact, and steps to reproduce it. Provide recommendations for remediation.
Risk Assessment: Assess the risk level of each vulnerability based on its potential impact and likelihood of exploitation.
b. Present Results
Executive Summary: Create an executive summary highlighting the key findings and overall security posture of the application.
Technical Presentation: Present detailed technical findings to the development team, providing guidance on how to fix the identified issues.
Best Tools for Mobile Application Penetration Testing
Using the right tools is crucial for effective mobile application pen-testing. Here are some of the best tools available:
1. MobSF (Mobile Security Framework)
- Platform: Android, iOS
- Features: MobSF is an automated, all-in-one mobile application pen-testing framework that provides static, dynamic, and malware analysis capabilities. It can analyze APKs, IPAs, and ZIP files containing source code.
2. Burp Suite
- Platform: Android, iOS
- Features: Burp Suite is a popular tool for web application security testing. Its powerful proxy capabilities allow for interception and modification of traffic between the mobile app and backend servers.
3. OWASP ZAP (Zed Attack Proxy)
- Platform: Android, iOS
- Features: OWASP ZAP is an open-source tool for finding security vulnerabilities in web applications. It can be used to intercept and analyze traffic, making it useful for mobile app pen-testing as well.
4. JADX
- Platform: Android
- Features: JADX is a decompiler that allows for reverse engineering of Android applications. It converts APK files into readable Java source code, helping to identify potential vulnerabilities.
5. Frida
- Platform: Android, iOS
- Features: Frida is a dynamic instrumentation toolkit that allows for the modification of running applications. It is useful for testing runtime security and bypassing security mechanisms.
6. Ghidra
- Platform: Android, iOS
- Features: Ghidra is a reverse engineering tool developed by the NSA. It provides capabilities for analyzing binary files and identifying vulnerabilities in compiled applications.
7. SoapUI
- Platform: Android, iOS
- Features: SoapUI is another tool for testing APIs. It provides comprehensive testing capabilities for REST and SOAP APIs, making it useful for mobile app pen-testing.
8. Nessus
- Platform: Android, iOS
- Features: Nessus is a comprehensive vulnerability scanner that helps in identifying security vulnerabilities within an application. It supports both static and dynamic analysis and provides detailed reports on identified vulnerabilities.
Conclusion
Mobile application penetration testing is a critical component of information security services, aimed at ensuring the security and integrity of mobile applications. With a structured approach and the right tools, security professionals can effectively identify and mitigate vulnerabilities. Regular pen-testing not only protects sensitive user data but also helps organizations comply with regulatory standards and maintain their reputation. As mobile applications continue to grow in complexity and usage, the importance of robust security measures, including penetration testing, cannot be overstated.