Exploring Mobile App Pen-Testing Methodologies for Secure Mobile App Development
In today’s digital age, healthcare organizations handle vast amounts of sensitive data, from patient medical records to financial information. Protecting this data is not only a legal requirement but also a crucial aspect of maintaining trust and operational integrity. This is where ISO 27001 Certification Services come into play. This certification is a globally recognized standard for information security management, providing a framework for managing and protecting sensitive information. For healthcare organizations, obtaining ISO 27001 certification is a strategic move to ensure robust data security, compliance, and patient trust.
Understanding Mobile App Pen-Testing:
Mobile App Penetration Testing, often abbreviated as pen-testing, is a systematic approach to evaluating the security of mobile applications. It entails replicating real-world attacks on the application to pinpoint vulnerabilities that malicious actors might exploit.
The primary goal of mobile app pen-testing is to uncover security weaknesses and provide actionable recommendations to enhance the app’s security posture.
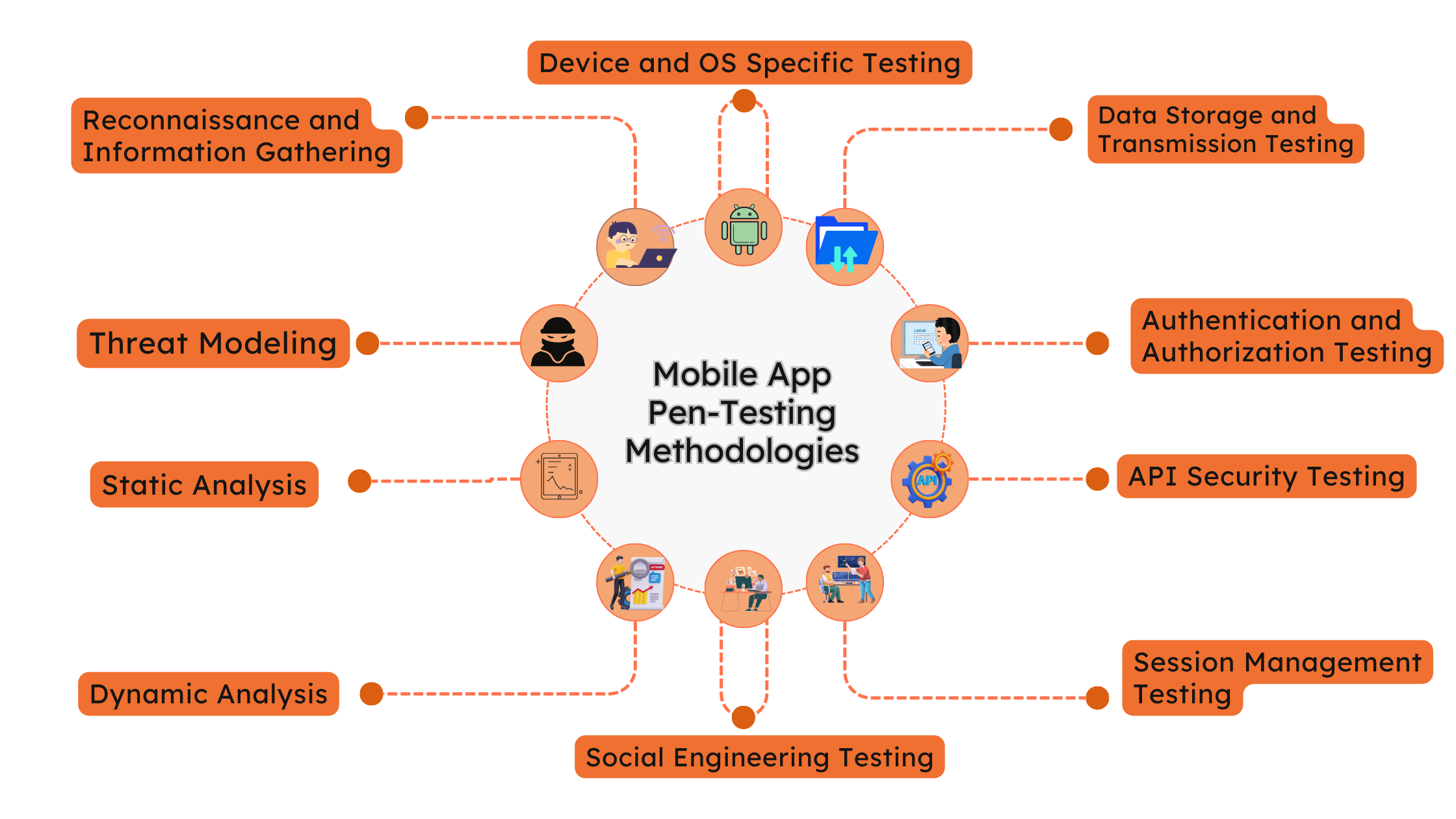
Methodologies in Mobile App Pen-Testing Services:
Reconnaissance and Information Gathering: The first step in mobile app pen-testing involves gathering information about the application, its functionalities, backend systems, APIs, and potential attack surfaces. This phase helps testers understand the app’s architecture and potential entry points for attacks.
Threat Modeling: Testers create a threat model specific to the mobile application, identifying potential threats, attack vectors, and critical assets. This step helps prioritize security testing efforts based on the most significant risks to the application.
Static Analysis: Static analysis involves examining the source code and application binaries without executing them. Testers employ automated tools to detect prevalent vulnerabilities like insecure data storage, inadequate input validation, and hardcoded credentials.
Dynamic Analysis: In dynamic analysis, testers interact with the mobile app in a controlled environment to identify runtime vulnerabilities. This includes testing for authentication bypass, session management flaws, insecure API usage, and improper data handling.
Data Storage and Transmission Testing: This phase focuses on evaluating how the mobile app stores sensitive data locally (on the device) and transmits it over the network. Testers assess encryption mechanisms, data leakage risks, and secure communication protocols.
Authentication and Authorization Testing: Testers evaluate the strength of authentication mechanisms such as biometrics, passwords, and multi-factor authentication. They also assess how the app enforces access control and privileges to ensure that only authorized users can access sensitive functionalities.
API Security Testing: Mobile apps often interact with backend APIs to fetch data or perform actions. Testers assess API endpoints for vulnerabilities such as injection attacks, insecure API keys, excessive permissions, and lack of rate limiting.
Session Management Testing: This phase examines how the app manages user sessions, including session tokens, cookies, and logout mechanisms. Testers look for session fixation, session hijacking, and session timeout issues that could compromise user sessions.
Device and OS Specific Testing: Testers evaluate the app’s behavior on different devices (Android, iOS) and operating system versions to ensure compatibility and security across platforms. They also test for platform-specific vulnerabilities and security best practices.
Social Engineering Testing: In this simulated attack scenario, testers attempt to manipulate users into disclosing sensitive information or performing actions that could compromise security. This includes phishing attacks, fake login screens, and social engineering tactics.
Benefits of Mobile App Pen-Testing Services:
Risk Mitigation: By identifying and addressing security vulnerabilities early in the development lifecycle, mobile app pen-testing helps mitigate the risk of data breaches, financial losses, and reputational damage.
Compliance Requirements: Many industries and regulatory standards (such as GDPR, HIPAA) mandate regular security testing for mobile applications. Pen-testing helps organizations meet compliance requirements and avoid legal penalties.
Enhanced User Trust: A secure mobile app builds trust among users, encouraging increased usage, positive reviews, and customer loyalty. Pen-testing demonstrates a commitment to user privacy and security.
Cost Savings: Detecting and fixing security issues during development is more cost-effective than dealing with a security incident after the app is deployed. Pen-testing helps organizations save money in the long run by avoiding costly security breaches.
Conclusion:
Mobile App Pen-Testing Services play a crucial role in ensuring the security and integrity of mobile applications. By following a systematic approach encompassing reconnaissance, threat modeling, static and dynamic analysis, data storage, and transmission testing, organizations can identify and remediate security vulnerabilities proactively. Investing in mobile app pen-testing not only protects user data but also strengthens the overall security posture of the application. For comprehensive information security services and robust mobile app pen-testing methodologies, partnering with experienced cybersecurity professionals is key to maintaining a secure mobile app ecosystem.