Ultimate Guide to Information Security & Continuity
Introduction to Information Security
Information security is more than just a buzzword; it’s a critical discipline dedicated to safeguarding sensitive data from unauthorized access, disclosure, alteration, and destruction. This section defines the core concepts and importance of information security in today’s interconnected world.
Significance:
- The significance of information security lies in safeguarding critical assets, including intellectual property, financial data, and personal information.
- It helps build trust among stakeholders, customers, and partners by ensuring that sensitive information is handled responsibly and securely.
- Protection of Confidentiality, Integrity, and Availability:
- Information security aims to uphold the principles of the CIA triad: Confidentiality (ensuring data is only accessible to authorised entities), Integrity (maintaining the accuracy and trustworthiness of data), and Availability (ensuring timely and reliable access to data.
- Information security aims to uphold the principles of the CIA triad: Confidentiality (ensuring data is only accessible to authorised entities), Integrity (maintaining the accuracy and trustworthiness of data), and Availability (ensuring timely and reliable access to data.
Evolving Landscape of Cybersecurity Threats:

- Dynamic Nature of Cyber Threats:
- The cybersecurity landscape is dynamic, characterised by constant evolution in the tactics, techniques, and procedures employed by cybercriminals.
- Threats are no longer static; they adapt to technological advancements and exploit vulnerabilities in new and sophisticated ways.
- Motivations of Threat Actors:
- Understanding the motivations behind cyber threats is crucial. Web Security Threat actors may include hackers seeking financial gain, state-sponsored entities pursuing political objectives, or activists aiming to make a social or political statement.
- Recognizing these motivations helps in tailoring effective security measures and responses.
- Common Attack Vectors:
- Cyber threats manifest through various attack vectors, including phishing, malware, ransomware, and social engineering.
- The evolving landscape introduces new attack vectors, such as supply chain attacks and zero-day exploits, demanding continuous adaptation of cybersecurity strategies.
- Adoption of Advanced Technologies:
- As organisations embrace advanced technologies like artificial intelligence, IoT, and cloud computing, cyber threats adapt to exploit vulnerabilities in these domains.
- The interconnectedness of systems and the increasing attack surface require a proactive and holistic approach to cybersecurity.
- Global Nature of Cyber Threats:
- Cybersecurity is a global concern as cyber threats surpass geographical confines, recognizing no borders. Threat intelligence sharing and international cooperation are essential for a collective defence against cyber adversaries.
- The interconnected nature of the internet necessitates a collaborative effort to address cyber threats effectively.
Foundations of Cybersecurity
The foundations of cybersecurity constitute a multidimensional framework aimed at fortifying the digital realm against an array of evolving threats, especially in the context of cybersecurity online. At its heart lies the CIA Triad—Confidentiality, Integrity, and Availability—serving as the fundamental principles guiding protective measures. Confidentiality safeguards sensitive information from unauthorized access, employing encryption and access controls—critical aspects of cyber security online that help protect data from potential breaches and ensure user privacy. Integrity, a cornerstone in online security, ensures data accuracy and trustworthiness, employing techniques like hashing and digital signatures to verify the authenticity of information exchanged over the internet.
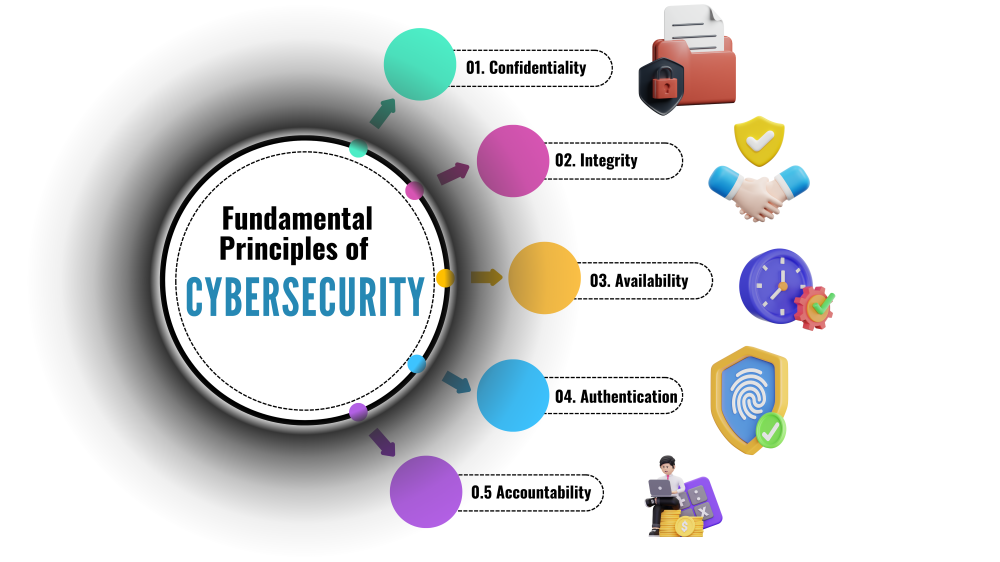
- Confidentiality: Secures information accessibility exclusively for authorized individuals or systems through practices like encryption, access controls, and data classification
- Integrity: Integrity in digital security is paramount, emphasizing the preservation of the accuracy and trustworthiness of information. Our approach to digital security encompasses a robust framework that not only safeguards data but also ensures its unaltered and reliable state over time. Involves mechanisms like checksums, digital signatures, and version control.
- Availability:
- Ensures that information and systems are accessible and usable when needed.
- Involves measures such as redundancy, disaster recovery planning, and DDoS protection.
- Authentication:
- Verifies the identity of users or systems accessing information or resources
- Encompasses approaches such as passwords, biometrics, and multi-factor authentication methods
- Accountability:
- Traces and logs activities to establish responsibility for actions taken within a system.
- Involves audit trails, logging mechanisms, and security information and event management (SIEM) systems.
Risk Assessment Methodologies
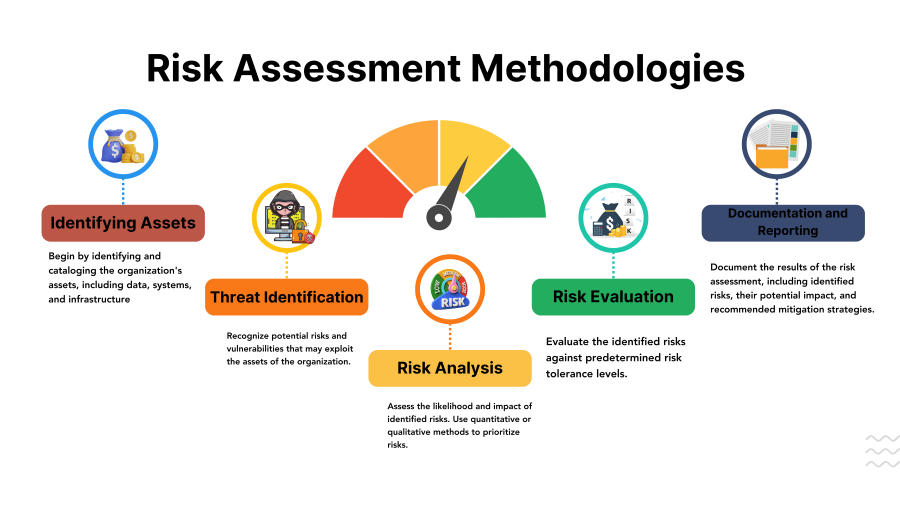
- Identifying Assets:
- Begin by identifying and cataloging the organization’s assets, including data, systems, and infrastructure.
- Classify assets based on their importance and sensitivity.
- Threat Identification:
- Recognize potential risks and vulnerabilities that may exploit the assets of the organization.
- Consider internal and external threats, natural disasters, human error, and malicious activities.
- Risk Analysis:
- Assess the likelihood and impact of identified risks. Use quantitative or qualitative methods to prioritize risks.
- Calculate the risk level by multiplying the likelihood and impact scores.
- Risk Evaluation:
- Evaluate the identified risks against predetermined risk tolerance levels.
- Determine which risks are acceptable, require mitigation, or necessitate risk transfer or acceptance.
- Documentation and Reporting:
- Document the results of the risk assessment, including identified risks, their potential impact, and recommended mitigation strategies.
- Provide clear and concise reports to stakeholders for informed decision-making.
Strategies for Risk Mitigation and Management
In the dynamic landscape of information security management, effective risk mitigation is crucial for maintaining a secure and resilient environment. Incorporating key strategies ensures a proactive stance towards identified risks.
- Risk Mitigation Strategies:
- Implement preventive measures to reduce the likelihood or impact of identified risks.
- Examples include implementing security controls, conducting regular security training, and enforcing access controls.
- Risk Transfer:
- Transfer certain risks through insurance policies or outsourcing specific functions to third-party providers.
- Ensure contractual agreements clearly define responsibilities and liabilities.
- Risk Acceptance:
- Acknowledge certain risks as unavoidable or acceptable based on the risk tolerance of the organization.
- Develop contingency plans for managing these accepted risks.
- Continuous Monitoring and Review:
- Establish a process for continuous monitoring of risks, reassessing the risk landscape regularly.
- Adjust risk management strategies based on changes in the organization’s environment or threat landscape.
- Incident Response Planning:
- Develop and regularly test incident response plans to ensure an effective and coordinated response to security incidents.
- Integrate incident response into overall risk management strategies.
Network Security: